Jump to
Stay tuned for
more insights
Follow us on
SSH Tunneling for Pentesters
Establishing a source IP is an important part of most pentest engagements. Many customers want to know your IP for whitelisting purposes.
Using SSH tunneling is a great way to quickly allow multiple pentesters to share an IP with the overhead of VPN servers or clients.
Method 1 – Basic SSH Tunnel with Putty
This method will route your web traffic through the SSH server, allowing your web traffic to masquerade behind your jump box.
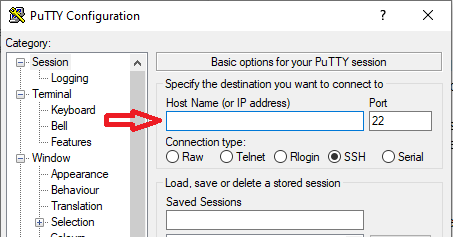
Step 1
Add your SSH server’s IP and port
Step 2
Navigate to Connection -> SSH -> Tunnels. Add a local source port, and set Dynamic. This port will open on your local machine; we will later point our browser to use this as the proxy.

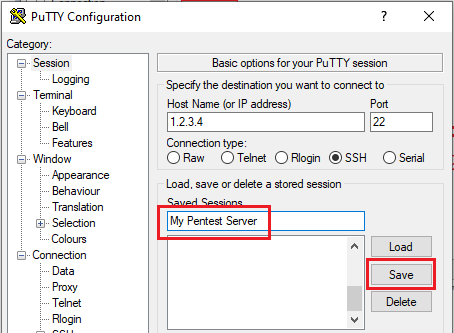
Step 3
Head back to Session, add a name, and hit save.
Browser Configuration
To make our lives much easier during pentesting activities, we will use foxyproxy to switch back and forth between proxies as needed.
We simply fill in a name, select Socks5, and use 127.0.0.1 port 9999 as the proxy server.

Method 2 – Multi-hop or “Nested” SSH Tunnels
In this example we want to masquerade behind a server which is only accessible via multiple SSH hops. To do this we do the following:
Create an ssh tunnel with local port forwarding. This will use our SSH session to open a tunnel to the second pentest jump box.
We will open a second SSH session to 127.0.0.1:2222 (this now points to our second pentest jump box). This SSH session will use a
dynamictunnel to allow us to masquerade behind the second hop.
Step 1
Create a new profile in Putty to your jump box. This will be the first of two we will need. This time we will add a Local tunnel as follows:

Save this profile and open the connection.
Step 2
Create a second Putty profile. This time, the destination is 127.0.0.1:2222. Remember, this is now forwarding to the jump box.

Step 3
Now add the dynamic tunnel to this as we did in method 1.

You should now be able to send your traffic with an origin of 2.3.4.5 (which passes through 1.2.3.4).
Conclusion
Although these methods are used often for pentesting, they can be applied to many other use cases.
