Jump to
Stay tuned for
more insights
Follow us on
iOS Frida Objection Pentesting Cheat Sheet
A quick and simple guide for using the most common objection pentesting functions. Penetration testers can use this to quickly find the majority of vulnerabilities in iOS applications.
Usage / Installation
Pre-Install – You need Frida to use objection
If using for the first time, remember that you have two way of using Frida:
- A Jailbroken device with Frida server (preferably connected via USB). You can install Frida server from Cydia. To jailbreak you device check our ios jailbreak guide.
- Using an app with the Frida agent injected into the IPA (for non-jailbroken devices).
Install Objection
Installation is easy!
pip3 install objectionCheck Device Connectivity
Check to make sure the device is successfully connected over USB. If you have

Check Installed Apps
List installed applications:
~$ frida-ps -Uai
PID Name Identifier
---- ---------------- -------------------------------
5948 Cydia com.saurik.Cydia
5829 Mail com.apple.mobilemail
5945 Settings com.apple.Preferences
- App Store com.apple.AppStore
- BBQ Go com.bbqGo
- Books com.apple.iBooks
- Calendar com.apple.mobilecal
- Camera com.apple.cameraStart Objection and Attach to a Process
Objection will restart the app if required and inject into the process.
~$ objection -g com.client.mytestapp explore
Using USB device `iOS Device`
Agent injected and responds ok!
_ _ _ _
___| |_|_|___ ___| |_|_|___ ___
| . | . | | -_| _| _| | . | |
|___|___| |___|___|_| |_|___|_|_|
|___|(object)inject(ion) v1.9.4
Runtime Mobile Exploration
by: @leonjza from @sensepost
[tab] for command suggestions
com.client.mytestapp on (iPad: 12.4.7) [usb] #Disable Certificate Pinning
Certificate pinning can prevent an application from accepting your proxy’s SSL certificate and can restrict your ability to proxy web traffic. For penetration testers that need to get things done quickly, this can be a real pain.
Objection is our best recommendation and first approach to remove certificate pinning on iOS
Pro tip: use --quiet since this hook can generate a lot of noise throughout your testing.
[usb] # ios sslpinning disable --quiet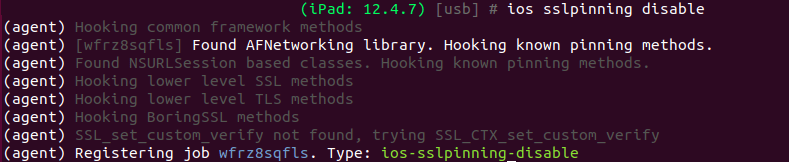
Congrats, your certificate pinning is now disabled!
Inspect Binary Info
Dump info on the iOS binary. This will allow you to confirm if the app is encrypted and compiled as a Position Independent Executable (PIE):
[usb] # ios info binary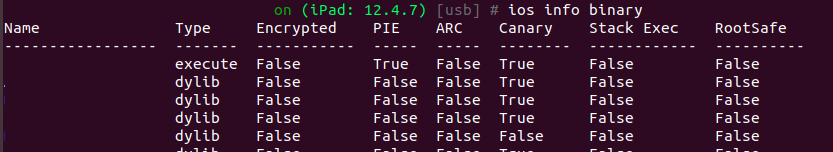
Dump the App Keychain
Assessing keychain storage is a necessity for iOS pentests. You can dump the app keychain and its contents to review settings:
[usb] # ios keychain dump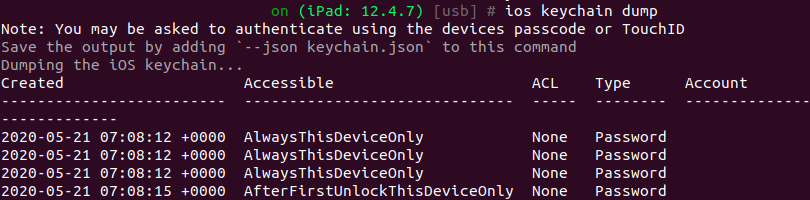
Explore the App Structure
Objection is also great to quickly explore the IPA package structure. As part of any pentest you will want to review the package for sensitive data, API keys, and other information disclosure in application files.
Navigate the Directories
You can list directories from the REPL with ls:
[usb] # lsExamine files with file cat:
[usb] # file cat examplefile.txtExplore plist Files
Plist files should be examined for sensitive information.
[usb] # ios plist cat Info.plistCheck for Other data stores for sensitive information
Check for sensitive data in NSURLCredentialStorage
[usb] # ios nsurlcredentialstorage dumpCheck for sensitive data in NSUserDefaults
[usb] # ios nsuserdefaults getCheck for secure flags and sensitive data stored in cookies:
[usb] # ios cookies get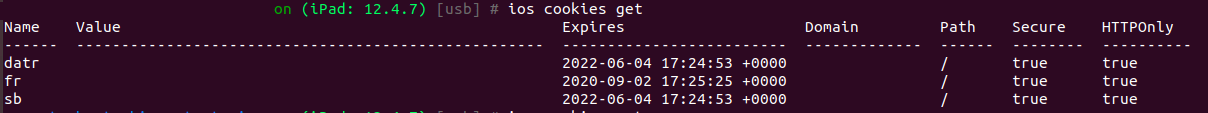
As you can see, Objection is a great tool to quickly identify a significant number of iOS pentesting test cases. Stay tuned, shortly we will follow up with examples of hooking and patching apps with objection.
Troubleshooting
If you receive the following error you will need to go to Settings -> Profiles & Device Management and verify the app.
Unable to connect to the frida server: unable to launch iOS app: The operation
couldn’t be completed. Unable to launch com.myapp because it has an invalid code
signature, inadequate entitlements or its profile has not been explicitly trusted
by the user.