Jump to
Stay tuned for
more insights
Follow us on
Essential Wireshark Skills for Pentesting
Wireshark is an essential tool for pentesting thick clients and most things in a Windows environment. Having a solid understanding of the capabilities can improve the speed and effectiveness of your pentesting. We will cover a few key functions of Wireshark that come in handy in penetration tests.
1. Capture vs Display Filters
In most scenarios during a pentest you will be looking for specific traffic. High traffic networks and applications can overwhelm Wireshark and you with excessive traffic. Using a capture filter instead of a display filter can remove lots of the traffic you don’t care for and help find what you’re looking for faster.
Remember these two differences between the two:
Capture filters – completely ignore traffic set by the filter. Display filters – filters existing captured traffic, opening the filter in a new window.
To create a capture filter click the capture option icon and select the interface you want. This is usually the interface which shows active traffic in the status graph.
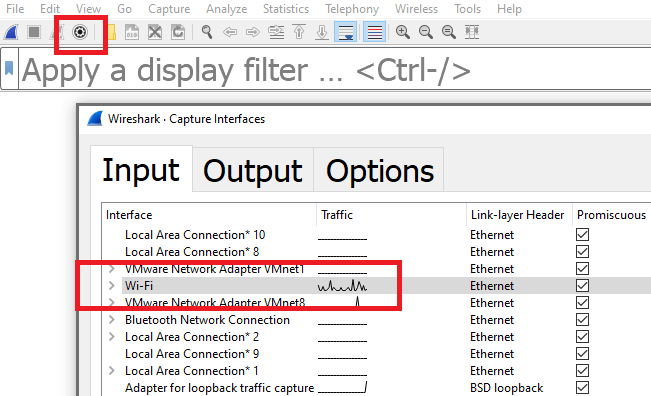
Enter the capture filter in the text area below:

Note: capture filters do not support protocol specific filtering. You may be limited to filtering based off port 80 instead of HTTP.
2. ‘Follow’ Traffic Streams
The traffic you’re interested in will often be spread out over a number of inbound and outbound packets. This can be frustrating when trying to view sensitive HTTP request/response pairs and most application level data in general.
Fortunately Wireshark allows you to select a packet and view the entire TCP stream it belongs to.
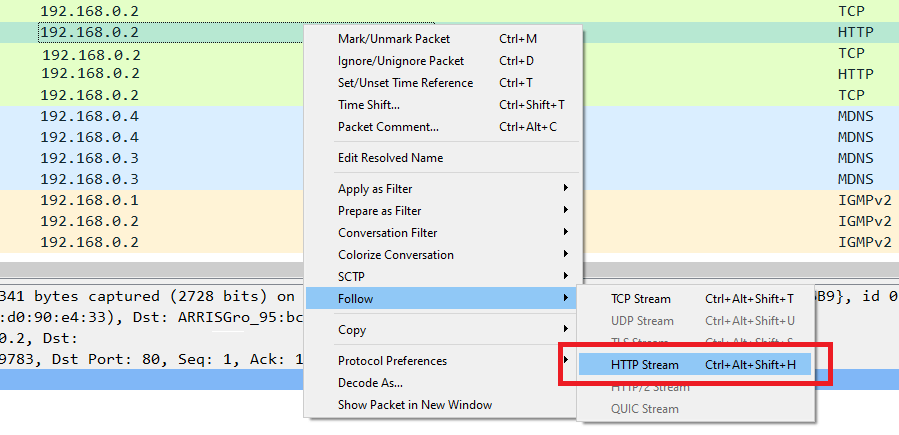
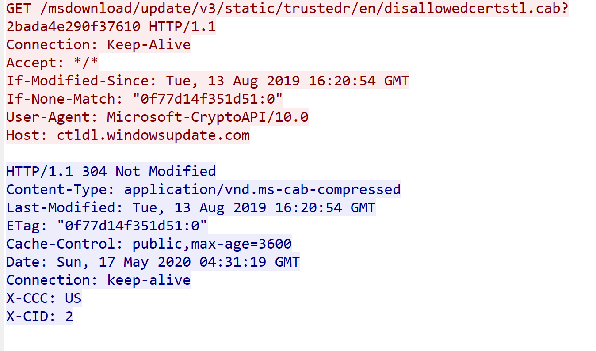
Inbound and outbound traffic will be highlighted in red and blue to show the application layer communication without packet headers.
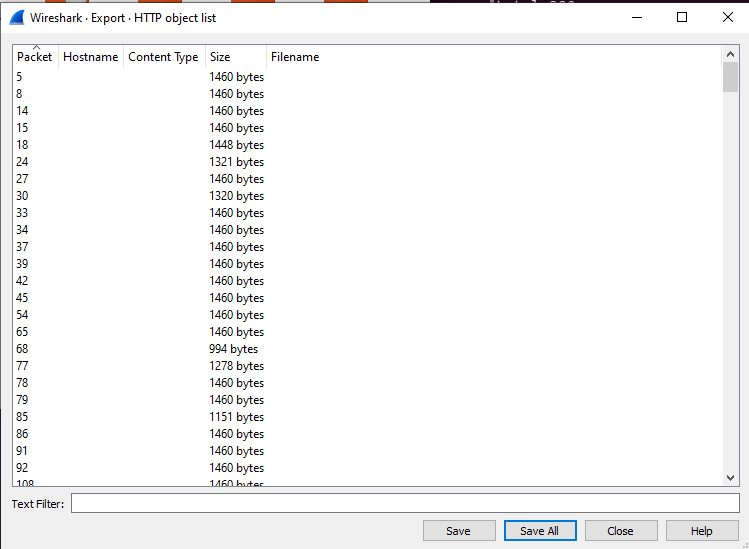
3. Exporting Objects
Often during a pentest you may be looking to grab sensitive information from plain text streams. Wireshark has an “Export objects” function that combines protocol dissectors with content extractors to dump objects contained in streams. This can often reveal Jpegs from video streams, PDFs from HTTP downloads, and so on.
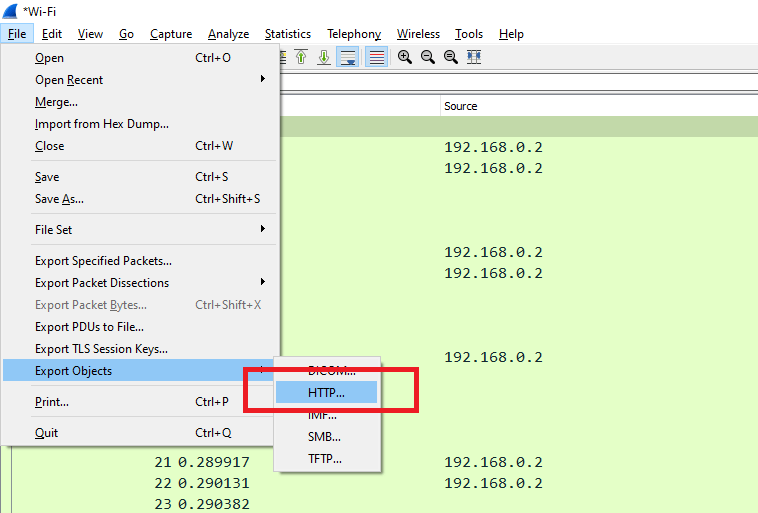
A list of objects which can be extracted will be shown below:
4. Remember – .pcap Files Are Universal
Always remember that pcap files are not proprietary to Wireshark. As a pentester you surely will find it often more convenient to use tcpdump as a collector and use Wireshark on a different system to analyze the traffic.
$ sudo tcpdump -i ens33 -w out.pcapNote: 90’s kids may recall having to set specific spaplen values for tcpdump to log entire data payloads. Tcpdump no longer truncates packet payloads and you can safely collect entire packet payloads with the command above.
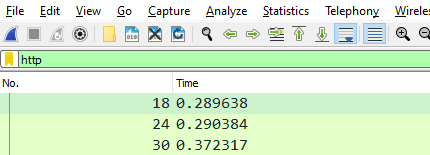
5. Useful Display Filters
Display filters are your key to quickly sort through and analyze traffic streams. Below are some filters any pentester is sure to need:
View plain-text HTTP traffic
Exclude traffic from an IP:
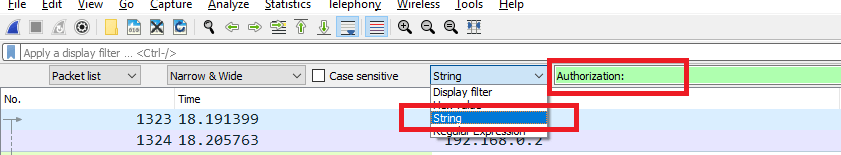
! (ip.addr == 192.168.0.2)6. Searching for Strings
Searching for strings is not entirely trivial. Hitting Ctrl+F will bring up the search bar, however you must select string from the dropdown to search packet payloads for ascii strings.
References: https://wiki.wireshark.org/
