Jump to
Stay tuned for
more insights
Follow us on
Defeating Android Emulator Detection
At some point while performing vulnerability assessments on android applications you will encounter apps that don’t want to be run within an emulator. We can’t blame application owners for wanting to ensure that the user interaction they see comes from genuine devices, but it doesn’t help us do any security testing on it. There are several ways to detect an emulator; however this example is only relevant to the most common way we see. In this application, a check is performed for an IMEI value of 000000000000000 which is the value used by the emulator that ships with the Android SDK. The code segment below checks for this value and exits if true. While we could easily patch the value from within the application, it may be more efficient in the long run to simply change the IMEI value of our emulator. This way we don’t have to patch the next application that does this.
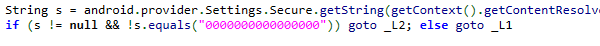
The IMEI is stored as a text string, so we will search for a ‘text string’ accordingly. Open the binary with hexeditor, hit ^W, and search for the fifteen zeroes. Note that the binary we wish to open is not the “emulator” binary, but the “emulator-arm” binary. If you are using a different architecture you may be using the mips or x86 binary.
cp emulator-arm emulator-arm.bak
hexeditor emulator-arm
^W
Note once again this is an ascii string, so the zeroes are 0x30.
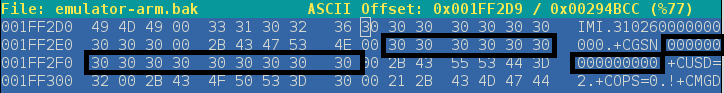
In this case, we just replace four characters with 1234 by updating 0x31, 0x32, 0x33, and 0x34. Do not change the length of data in this segment or overwrite bytes outside this segment or you will corrupt the binary.
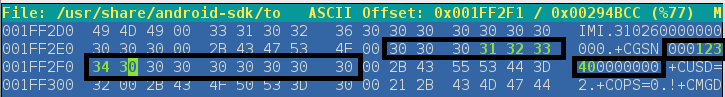
Just save and exit. Now our emulator will be using our new custom value.
