POST /profile HTTP/2
Host: example.com
first_name=john&last_name=doe|
API Penetration Testing

JUMP TO
What is API penetration testing?
An API penetration test is a process to identify security vulnerabilities in an API. It is designed to determine if an API is susceptible to vulnerabilities that may include the following:
Sensitive information disclosure
Broken authentication
API Mass Assignment
SQL Injection and other input validation flaws
Bypass of access controls
API pentests are performed on a wide variety of protocols and schemes including REST, SOAP, and RPC.
API pentesting vs application pentesting
API Penetration Testing is a closely related assessment to application penetration testing. However, while many of the tasks performed in these assessments overlap, there are key differences that are unique to API frameworks and design patterns.
In many cases, an “API pentest” is implicitly performed as part of an application pentest. But other times, a standalone API may warrant a more tailored API penetration test.
This is typically determined during a scoping process.
API pentest scoping
As with application pentesting, API pentest scoping is as important as the pentest itself. Critical preparations must be made, such as:
01
Deciding if a client is necessary to generate and send requests to the API.
02
Understanding what API documentation exists and what can be provided.
03
Understanding roles, authentication methods, and API design.
When engaging a pentest company there are many key decisions to make as to how the pentest is both performed and delivered.
Common API vulnerabilities
Information disclosure
APIs often reveal more information than they should. API responses are notorious for revealing excessive and sometimes dangerous amounts of information.
"email":"john.doe@example.com", "first_name":"john", "last_name":"doe", "lat": "40.746657", "long":"-73.964341", "password":"f3bbbd66a63d4bf1747940578ec3d0103530e21d", "role":"admin"An API pentest should ask questions such as:
- Should password hashes be disclosed to users?
- Should users see the locations of other users?
It’s an easy pitfall for developers to encounter where API responses return the entire state of an object rather than the minimum amount of information necessary for users to have.
API mass assignment
API Mass Assignment is a condition where a client can overwrite server-side variables that the application should not allow. This is often a high risk vulnerability that can allow users to escalate privileges and manipulate business logic.
Request
Response
Request
Response
"first_name":"john", "last_name":“doe", "role":"provider"Request
POST /profile HTTP/2 Host: example.com first_name=john&last_name=doe&role=admin|Response
"first_name":"john", "last_name":“doe", "role":"admin"API authentication vulnerabilities
API authentication schemes have unique security requirements as well. A holistic API pentest should review how access tokens are generated and revoked, and dive into specific weaknesses of those tokens.
API pentesting and XSS
Cross-site Scripting (XSS) is a ubiquitous vulnerability on pentest reports. As you might have guessed, this problem is still very relevant to APIs. But things are not so black and white when dealing with an API.
For example, can you tell if the following response indicates an XSS vulnerability?
HTTP/1.1 200 OK [..] {"name":"bob<script>alert(1)</script>"The answer actually depends on the Content-Type header. If the following Content-Type is set, the API would not be vulnerable:
Content-Type: application/json; charset=utf-8However, a Content-Type treating the response as HTML would, in fact, be vulnerable:
Content-Type: text/htmlAPI pentesting and CSRF
Cross-Site Request Forgery (CSRF) may also be identified during an API penetration test. Like XSS, a number of behaviors must be reviewed to determine if the finding is valid.
These include behaviors such as:
- Does the API require JSON? Or can POST parameters be substituted?
- Is a Content-Type request header such as application/json enforced?
- Are cookies in use and do they use SameSite properties?
- Does the application reject malformed JSON?
Cors policies
Cross-Origin Resource Sharing (CORS) is also a common source of misconfigurations. CORS is a specification to relax the same-origin policy enforced by browsers.
Care must be taken to ensure that an overly permissive CORS policy does not undermine API security.
API pentesting tools
Diving into the mechanics of testing, the core tools used for API Pentests are largely the same as general application testing. Frameworks like BurpSuite are commonly used to tamper with parameters and scan requests.
But the most meaningful API testing is done when integrating Postman or Swagger UI with these testing frameworks. Postman, as shown below, will typically be configured to use Burp via system proxy settings.
A screenshot from Postman platform 
A screenshot from Swagger Petstore
Binding data securely
At some point, most API web-based applications will ‘bind’ data. This takes an API response and includes it in the DOM shown on screen to users.
For web-based applications using APIs, data binding methods can be a critical area of security. This also highlights an important relationship that exists between web-based clients and their API.
Let’s compare the safe and dangerous ways to bind the API response for the username
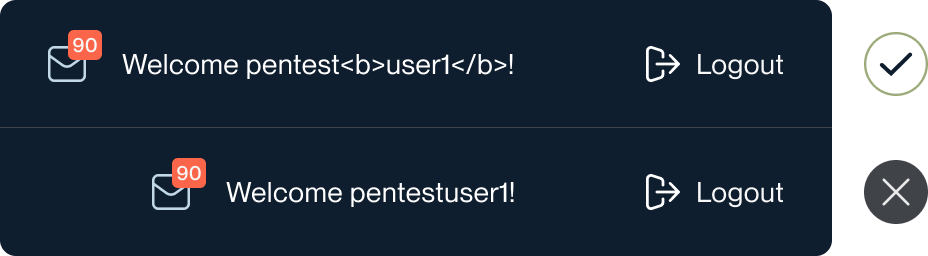
API rate limiting
APIs are frequent targets of abuse, especially when intended for public use. Rate limiting has become a vital defense for large API providers to deter bots and other automated attacks.
An API pentest seeks to identify endpoints which may be susceptible to automated attacks and recommend rate limiting accordingly.
Below shows an example response to excessive requests:
HTTP/1.1 429 Too Many Requests Content-Type: text/html Retry-After: 3600
Conclusion
API Pentesting is a complex process and highly subjective to the design of each API. These topics should help provide guidance for both performing or contracting a better API pentest.
If you’re looking for help on how to better assess an API, check out our pentest services and drop us a line.
