Jump to
Stay tuned for
more insights
Follow us on
GET vs POST
GET and POST request methods are ubiquitous in the love language of application pentesting (also known as HTTP). While GET and POST may be nothing more than arbitrary words, their meanings play an important role in the security of web-based applications.
HTTP Methods
Before diving into the details of GET vs POST requests, it’s important to understand HTTP and its concept of ‘methods’ (also referred to as ‘verbs’). Methods are required in the HTTP protocol and are used to indicate the nature of the request being made.
Although many methods exist (PUT, DELETE, OPTIONS, etc.), GET and POST represent the vast majority of requests made by web-based applications.
What is a GET request?
As the name suggests, GET requests are used to fetch content. This may be HTML content, images, or binary data. While GET requests often include parameters which may act as filters, they should not be used to perform persistent actions that alter the state of an application.
Example GET Request

Let’s dissect the request above.
As you can see, the first line specifies the method GET, the URI /search?user=alice, and the HTTP protocol version 1.1.
Also included the following headers:
- A
User-Agentheader (optional) – A self-reported client banner. - A
Hostheader – A host the client is intending to connect to. This mandatory HTTP 1.1 field is what allows multiple domains to be ‘virtually hosted’ on a single IP address.
What is a POST request?
In comparison to GET, POST is used to submit data to an application. For example, sending a username and password to login, or updating profile information. Usage of POST usually indicates a change of state is made to the application.
Example POST Request
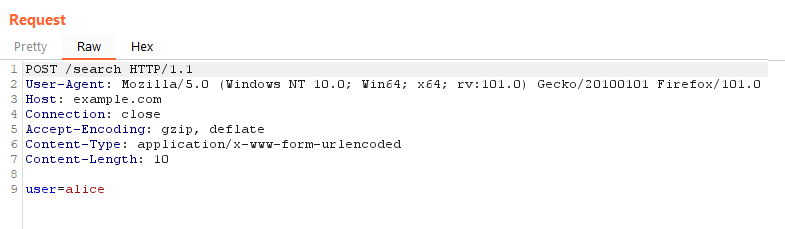
As you can see, query parameters no longer exist in the URI, and two new headers exist as well:
- A
Content-Typeheader – used to tell the server what type of data is in the payload. - A
Content-Lengthheader – used to tell the server how many bytes to read.
GET vs POST
There are two important differences between GET and POST requests that are most relevant to application pentesting:
- GET requests are easy to induce. Meaning an attacker can coerce a victim to make a GET request fairly easily. By embedding a URL in an
iframeorimgtag, it’s easy to force other users to make GET requests without their knowledge. This principle becomes very important to Cross-site Request Forgery attacks. - POST requests support a payload body. By supporting a payload section, data can be passed in a POST request without including it in the URL. It can also send larger payloads as well as binary data and file uploads.
GET, POST, and Penetration Testing
GET and POST requests have a variety of implications for application pentesting. To understand how these requests are manipulated during a penetration test, check out our guide to developing like a pentester.
